One Of The Best Tips About How To Detect Conficker C Worm
But security experts appeared correct in their.
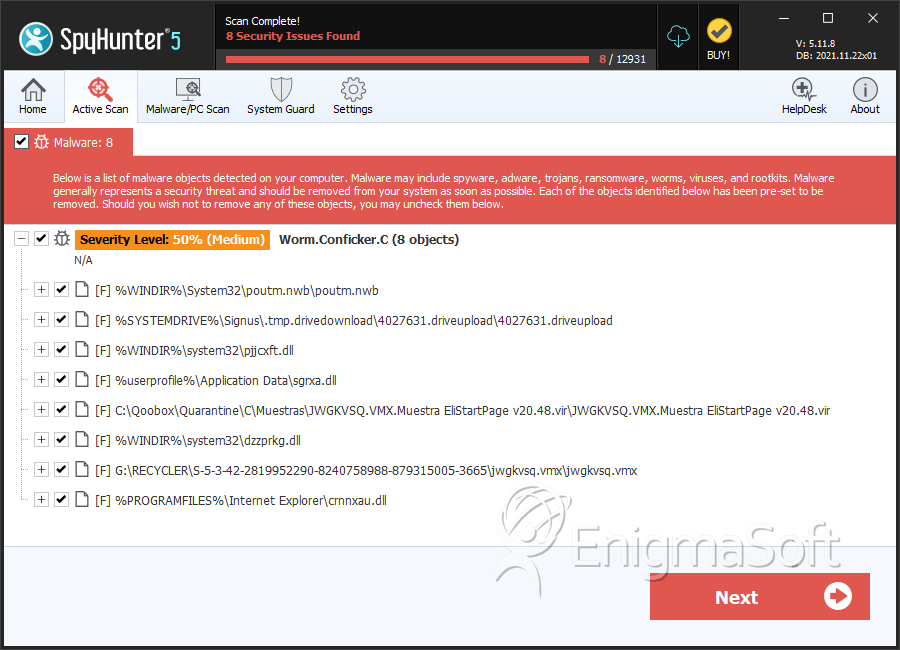
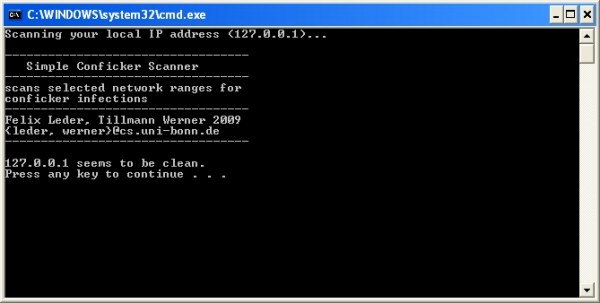
How to detect conficker c worm. The signatures folder contains yara rules to detect unpacked variants of the worm in memory and snort rules to detect exploitation attempts in a network. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. The presence of an infection may be detected if users are.
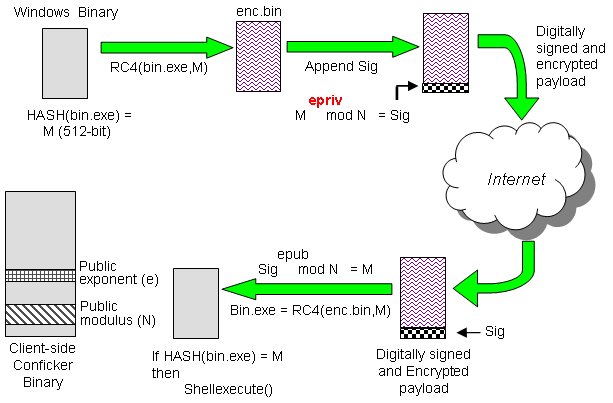
This worm has several capabilities which allow an attacker to execute arbitrary code on the remote operating. A typical invocation using this variable is: Conficker.c is a worm which exploits a vulnerability in the windows server service which allows remote code execution.
Up to 10% cash back download conficker worm fix. The remote host seems to be infected by the conficker worm. Malwarebytes can detect and remove worm.conficker without further user interaction.
Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008. The information in this knowledge base article is intended for business environmen… for detailed information about the conficker virus, visit the following microsoft web page: The conficker worm has become the malware that just won't die.
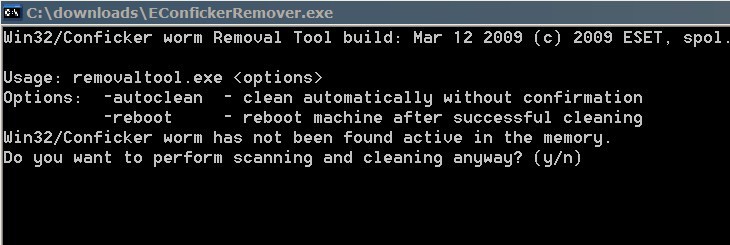
Security watchers at mcafee say that conficker is trying to communicate with master computers but isn't getting through. Even though more than 15 million ( some are saying more than 20 million) computers are infected, they are still saying it's not that bad, but trust me. Download our free removal tool:
To remove infected files, run the tool.









/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)



